The more of information there are, the more any business processes are tied to it, and the more painful its loss will affect the life of the company. It also happens that the loss of access to some data completely blocks the business operation. That is, access to information is a potential vulnerability, and if there is vulnerability, there will always be people who will try to take advantage of it.
According to 2018 data, 60% of companies in Kazakhstan have experienced at least one major cyber-attack in the past two years. One of the most common methods of cyber-attacks today are ransomware viruses, which are malware that enter the system through spam messages or some other vulnerable spots (most often, unfortunately, the human factor plays a decisive role) and encrypt all critical company data. In order to provide a code to decrypt the data, the attackers ask for a ransom, here we are talking about $5,000 or more. But even if the company decides to pay, it’s not at all certain that the hackers will fulfill their part of the deal. According to the experience of IT Support specialists, this is always a 50/50 chance. That is, you pay money for sure, but whether you will get access to your data again is a big question.
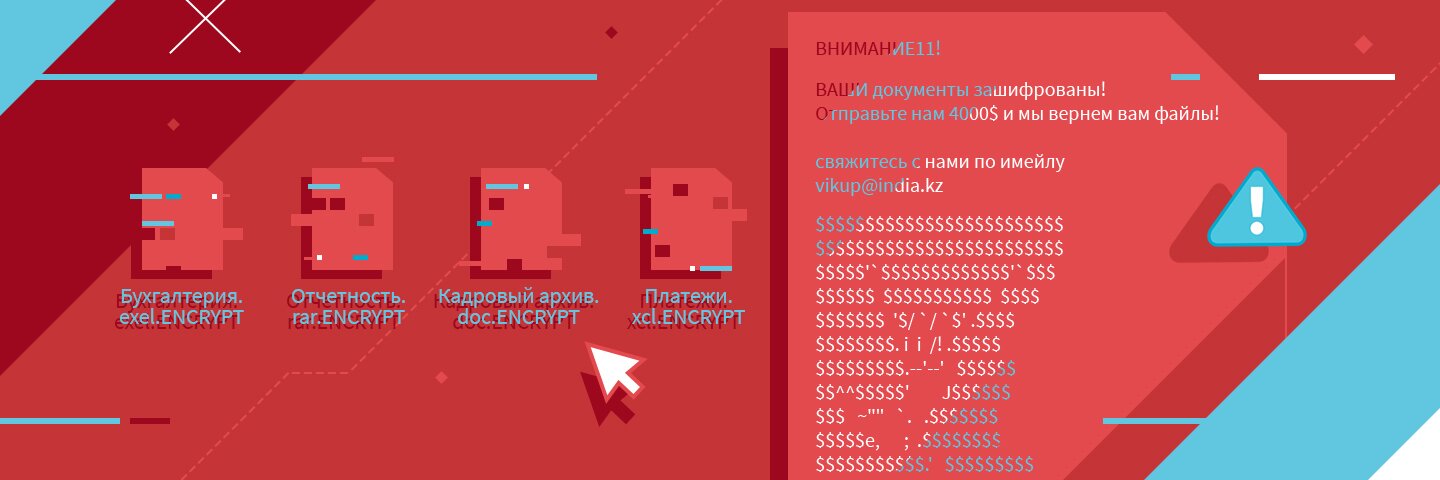
What are encoder viruses and how their attack goes
The principles of encoder viruses are simple: the user downloads and runs a malicious file, the virus spreads on the device on which it was “unzipped”, encrypts the main data (files with the extensions .jpg, .png, .doc, .xls, .dbf), then mirror servers, and then, if the backup is configured incorrectly, it spreads over the network to all workstations that it can reach. After encryption, a text file is created on the desktop or in each folder with encrypted files (for example, READ_ME !!!!!!. TXT), that says that the files are encrypted, and all attempts to decrypt them yourself will result in irrecoverable data loss. In the same file, the user finds the contacts of the hackers, usually a mail address, which must be contacted in order to find out the details of the ransom of the data. Most often, hackers demand to transfer money in Bitcoins (it’s almost impossible to trace this type transaction), and only after receiving the required amount they promise to send a decryption code. In most cases, it is useless to contact law enforcement agencies. The security forces are simply not prepared for this type of threat. According to the statistics of antivirus companies, it is possible to pick up the key, but only if we are talking about encryption ransomware 2–3 years old.
What if your system “caught” the ransomware?
· Don't try to rename files or change extensions. This will only make matters worse. If you really want to try to fix the situation yourself (you better not), you can make a copy of the encrypted file and try to experiment with it.
· Try to recover files from shadow copies. To do this, data recovery points must be created on your system. It is important to notice that very recent versions of ransomware can reach shadow copies too.
· Check your data backups. If the backup is configured correctly, then there is a chance that you have not lost any data at all.
· Contact antivirus companies for decryption codes. The problem is not new, and antivirus companies may have working keys for your version of the ransomware. In addition, leading antivirus companies provide decryption programs (for example, RectorDecryptor from Kaspersky Lab). According to the experience of IT Support, in Kazakhstan it is most effective to cooperate with Doctor Web.
How to protect yourself from ransomware?
At IT Support, there is never a month when specialists do not encounter ransomware. Most often, the vulnerability of the system is the employees with the least computer literacy. The ransomware can be contained in a letter with the subject “CV”, which will come to the HR department, or “Submit a tax report ASAP”, which will be sent to the accountant's mail. First of all, it is important to improve the general computer literacy of all employees in all departments of the company, to explain which letters can be opened and which absolutely must not. It is also necessary to install antivirus software and update it regularly. Important: in order to protect yourself from such “surprises” and not to overload non-core department employees with new information, you can restrict the ability to run some potentially dangerous files such as ones with the extensions .js, .cmd, .bat, .vba, .ps1 on all computers with “human vulnerability”. To do this, run the command gpedit.msc, then go to Computer Configuration – Windows Configuration – Security Settings – Application Control Policies – AppLocker – Script Rules, and using the wizard, create a new rule to prohibit the launch of all scripts for all users, for example, on the system drive. In addition, a correct backup can save the situation (we’ve talked about what mirroring and backup are in this article). After all, if the latest data at the time of the attack is saved on another device with a different operating system (or even better – under a separate user account, the password for which is known by one or two persons) outside the office and is not connected to the local network of the enterprise, then the attack is essentially not scary at all. Computers and the operating system work, you can create new files without access to the old ones, and the ransomware virus having fulfilled its function is automatically deactivated. Yes, the .kz domain zone is small, we are inconspicuous, and we do not participate in global wars for data. We are not interesting to anyone, and therefore have never faced serious threats, and this, in turn, allows the business to not worry too much about security. Yes, right now, data loss for businesses in Kazakhstan is not a big problem, but we are growing. The tables can turn pretty soon. Therefore, you need to have a tested and proven ability to quickly recover data, rather than using expensive (often unreasonably expensive) decryption technology.