IT outsourcing service system developed by IT Support Group.
On June 30, 2022, the «ASISTA» IT outsourcing service system became an object of intellectual property registered in the state registry of copyright-protected objects ©

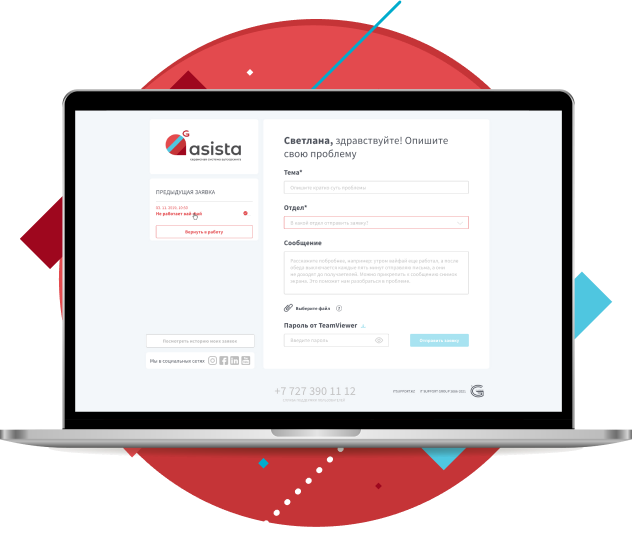
ITSM system developed for the Kazakhstani business space
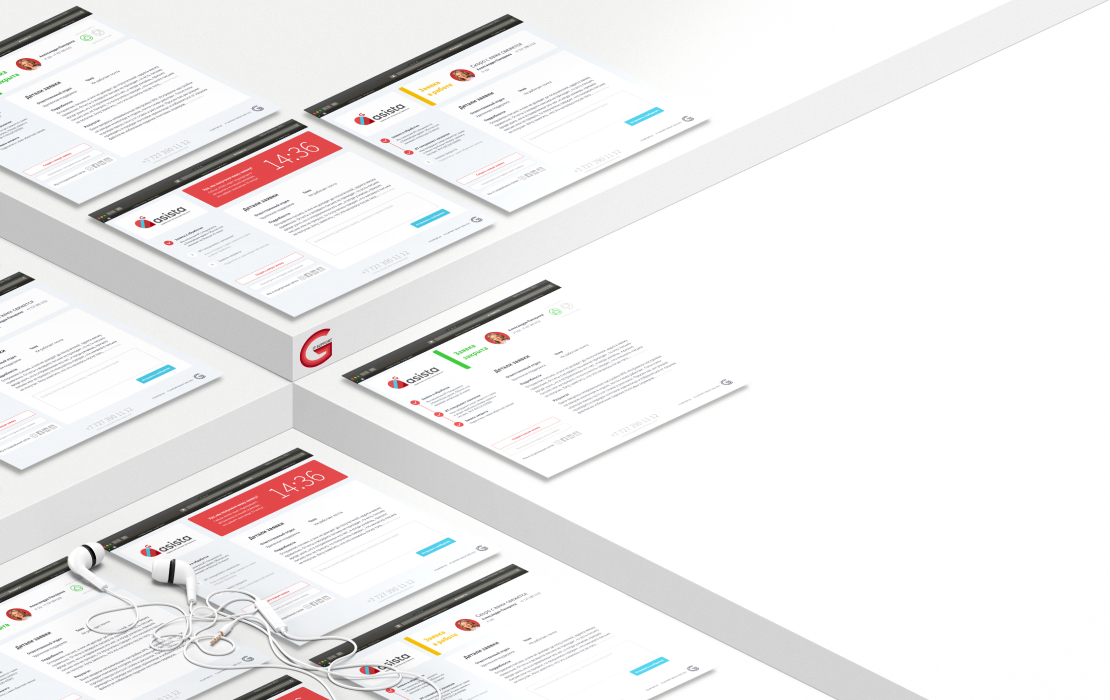
Asista is a communication system between IT Support Group and our clients. It helps create a comfortable environment for interaction, increases the efficiency of IT specialists work, and provides you with all the necessary information about our collaboration.

Asista is designed to make your interaction with IT specialists as convenient and effective as possible. Therefore, everything here is designed to speed up the processing of applications while giving you the ability to control the overall progress of the work.
Main functions
- Recognizes the user by ID
- Accepts applications via the web interface
- Creates applications in our CRM
- Sends notifications via email to users
- Shows the status of applications
- Provides convenient access to the archive of applications for an individual user or the entire company
- Shows convenient statistics on applications for a required period to make management decisions (BI);
- Helps in communication between the HR department and IT through the functionality of the access management module.


How to install Asista
Workflow algorithm
- You launch the Asista icon on your desktop, and the interface opens in your web browser.
- You select which of the service companies to submit a application to.
- You determine how to submit a application: restore an archived one, submit a new one, or return a previous one
- The specialist starts working on the application, and you can track its status.
- After the task is completed, you can rate the specialists work and leave feedback


Blog
General Manager of IT Support Group
Thank you!
Your request has been accepted for processing.
Our manager will contact you soon.